 Security Analysis with McCabe IQ Security Analysis with McCabe IQ
McCabe IQ is built for software engineers and security analysts who need to execute security or vulnerability analysis on complex software. Unlike other software security tools, McCabe IQ uses a path-oriented approach that enables engineers to understand interactions and verify exploitable paths within a codebase. This is crucial when determining exploitability, modeling attack space and performing vulnerability analysis.
McCabe IQ includes many features that can be used in the security analysis of your software. We recommend that your processes include the following:
- Analyze the Attack Surface Leveraging Path Analysis to determine the reachability, exploitability, and impact of vulnerable code (including visualization and structural complexity metrics); to determine the effectiveness of the testing of that attackable subset of code
- Analyze the effectiveness of security requirements testing or security tool testing using path coverage
- Compare complexity metrics with known vulnerable code to identify additional vulnerable code
 McCabe IQ is a critical tool for your security analysis, providing an understanding of your software’s control flow relative to vulnerable and exploitable code, including Attack Surfaces/ Targets/Maps/Trees. McCabe IQ is a critical tool for your security analysis, providing an understanding of your software’s control flow relative to vulnerable and exploitable code, including Attack Surfaces/ Targets/Maps/Trees.
Many types of security analysis and security testing tools exist, but most are limited in their code visualization and structural analysis capabilities. Most current analysis methods are not flow sensitive, context sensitive, or object sensitive. This leads to imprecision and thus to a high number of false alarms. A false negative is when the same vulnerability is exploited without being reported. This can occur if the tainted input is propagated along a different code path than in the sample exploit, or if the overwritten sensitive value is misused at a different location.
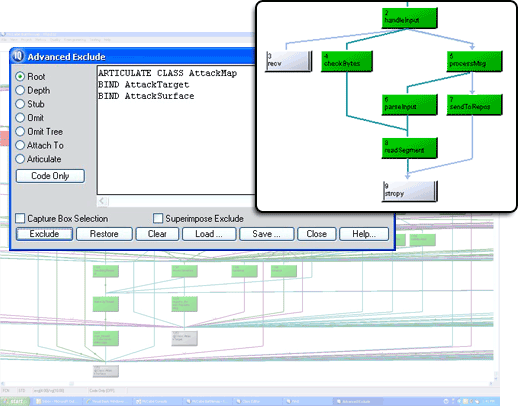
Typically, after a security tool points to a possible exploit, it is left up to the programmer to understand the code and design, determine the scope and nature of the exploit and then fix the bug in software that is often complex or, in other instances, developed by someone else. Security flaw exploitability means reachability and requires a security analyst to be cognizant of paths within code and design. Tools that aid an analyst in triage activities such as understanding the attack surface, the useable attack surface and attack trees are invaluable to software security - no other solution helps you understand your critical applications like McCabe IQ.
If you already have security tools deployed, McCabe IQ augments those tools and related processes, and helps you take full advantage of your overall investment in the security of your critical applications.
McCabe IQ has been the preeminent tool for modeling control flow and path analysis for decades. Its path-oriented nature can help you quickly understand the structure of your code and the testing of that code, as you analyze vulnerable and exploitable Attack Surfaces/Targets/Maps/Trees. McCabe IQ provides extensive control flow graphics depicting functional structure, class relationships, structural subtrees, and unit level flowgraphs. Its test path and execution code coverage information are tightly integrated and are overlaid on those same graphical views.
Use McCabe IQ to analyze the attack surface, leveraging path analysis to determine the reachability, exploitability, and impact of vulnerable code (including visualization and structural code metrics); compare complexity metrics with known vulnerable code to identify additional vulnerable code; and analyze the effectiveness of security requirements testing and security tools testing using path coverage.
McCabe IQ supports over a dozen languages, including the most commonly used (C, C++, Java/JSP, C#, VB, Ada). McCabe IQ provides over 100 metrics out of the box, with a focus on structural metrics and code coverage, including the McCabe-authored Cyclomatic complexity metric. Command line scripting, utilities, IDE integrations, and enterprise level reporting exist for enhanced automation.
Contact Us:
- To schedule a live demonstration or to speak with us about your software security requirements, Contact Us Here.
|
